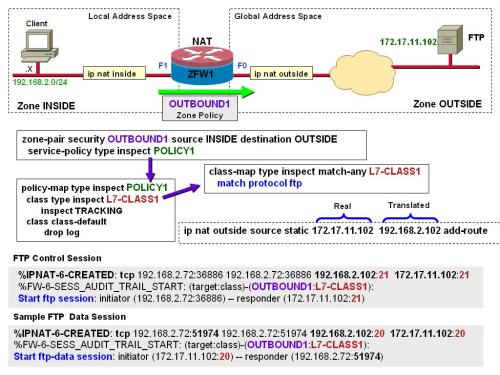
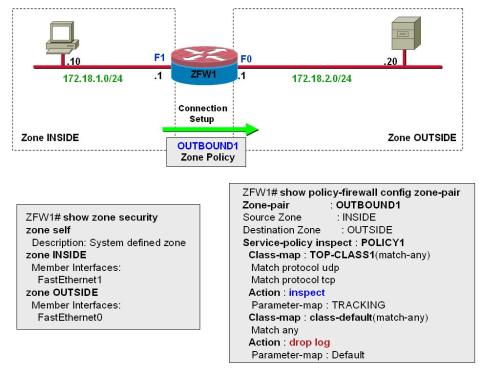
In the articles presented so far, we have studied situations in which inspected traffic is crossing the router-based firewall (instead of being directed to any of the router addresses).
The default operation of the Cisco Zone-based Policy Firewall (ZFW) is to allow traffic to an from the router interfaces, irrespectively of zone-pair security settings. If there is a need to modify this behavior, a system-defined zone, whose reserved name is self, must come into the scene.
Although interfaces are not directly assigned to the self zone, this special zone handles packets travelling from any router interface to a non-self zone (and conversely). You should keep in mind, though, that policies involving the self zone are still unidirectional.
Some facts about our reference topology are registered below:
- The policy construction employs the classic building blocks. The only particularity is that one of the interconnected zones is the self zone.
- The OUT-SELF zone-pair security is controlling packets sourced from the OUTSIDE zone and directed to the router interfaces. Packets originated by the router are not being inspected.
- Policies involving the self zone are more meaningful when they include L3 restrictions (materialized by ACLs).
- The activation of logging occurs in the same manner as already analyzed for non-self zones.

Inspecting router-bound traffic with the Cisco Zone-based Policy Firewall
** Topics for Study:
- Make sure you understand the handling of IOS object-groups.
- Revisit the post related to ACL integration into a ZFW scenario.
- Construct a ZFW policy to control traffic originated by the router and destined to the OUTSIDE zone. You should allow only ICMP Echo and Echo Reply messages from interface F0 to the 172.22.22.0/24 subnet.
- Update the ZFW policy analyzed in this post to limit telnet sessions going to the router. Telnet should only be allowed from sources located in the 172.21.21.0/24 subnet and directed to the Fo interface.
- Review the articles related to logging in the ZFW series (both for dropped packets and connection setup/teardown).
** Related Posts:
- Zone Firewall Series: https://alexandremspmoraes.wordpress.com/tag/zone-firewall/